Safe Signing 101
4 minutes
Oct 9th, 2022 - 10:16 am
Understanding The Message Signature
There are many misconceptions about signatures. In this article, I want to go over four types of message signatures to help users understand the risks associated with signing messages (also known as gasless signatures) on Ethereum or other EVM-compatible blockchains.
The Four Types of Signatures
These signature types are absolutely critical for all Ethereans in web3 to understand.
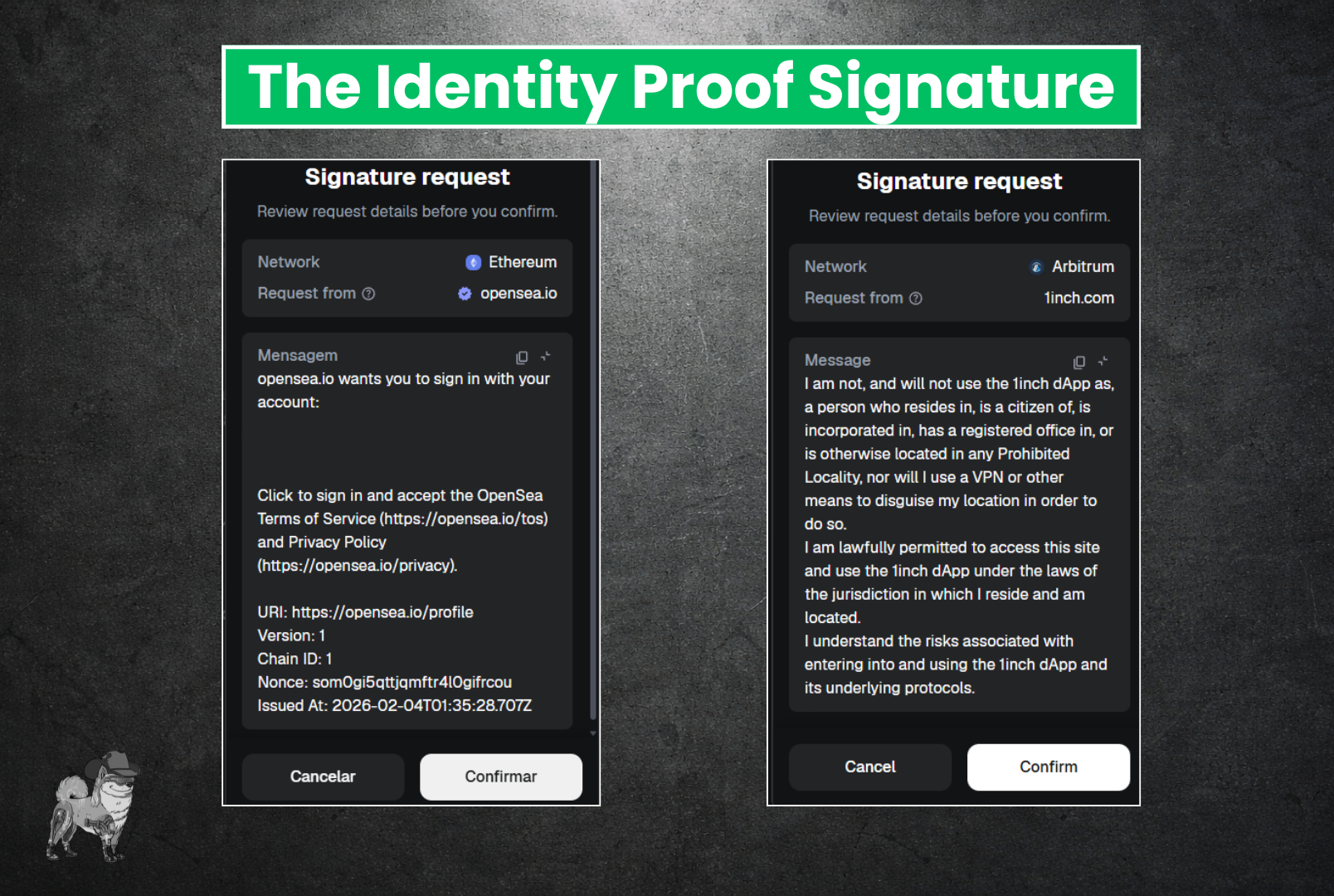
Type #1 - The Identity Proof (Safe)
This is mainly what signatures in web3 are used for. Although there is no unifying standard for what these look like, some common elements include a Terms of Service, your Wallet address, a nonce to prevent replay attacks, and sometimes a short string to ensure the message you are signing on the software wallet matches the message on the hardware wallet. See a couple examples below:
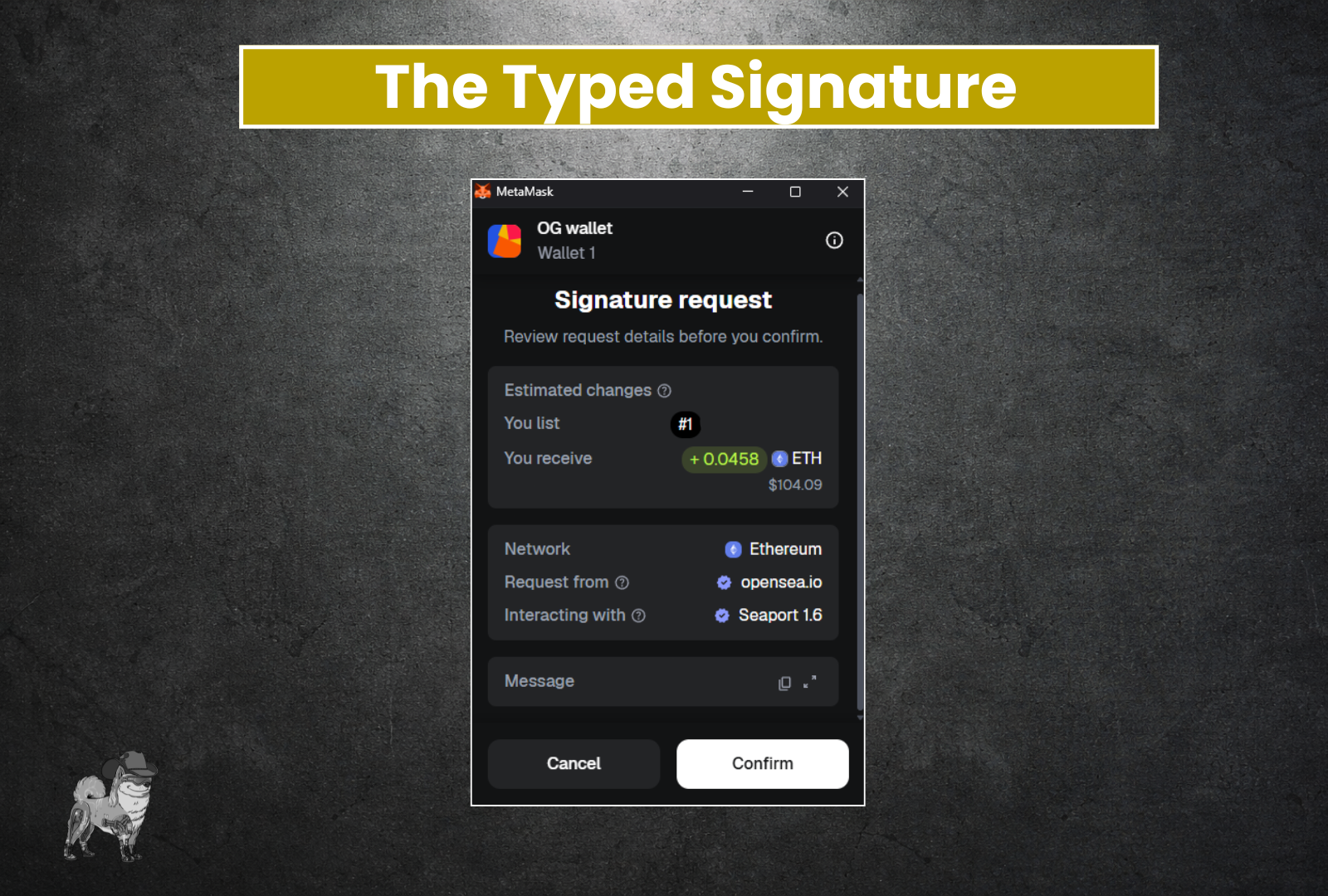
Type #2 - The Typed Signature [Smart Contract Interaction] (Use Caution)
Often some part of smart contracts rely on signatures off-chain to make things happen. These types of signatures will break down all the inputs that will be part of the contract interaction. Quite handy, but this is where if you have open approvals (or “Permittable” tokens, as explained in the “All-About-Approvals” article) you need to be careful. Although you can tell exactly what they are doing in this example, you need to ensure the source that is surfacing these kinds of signature requests is reputable.
For example, if you got the pictured signature approval request outside of Opensea, you should be very worried, and never sign it. This is particularly true if you are using your “Marketplace/Sell” wallet address, as we introduced in our “Wallet For Every Occasion” article.
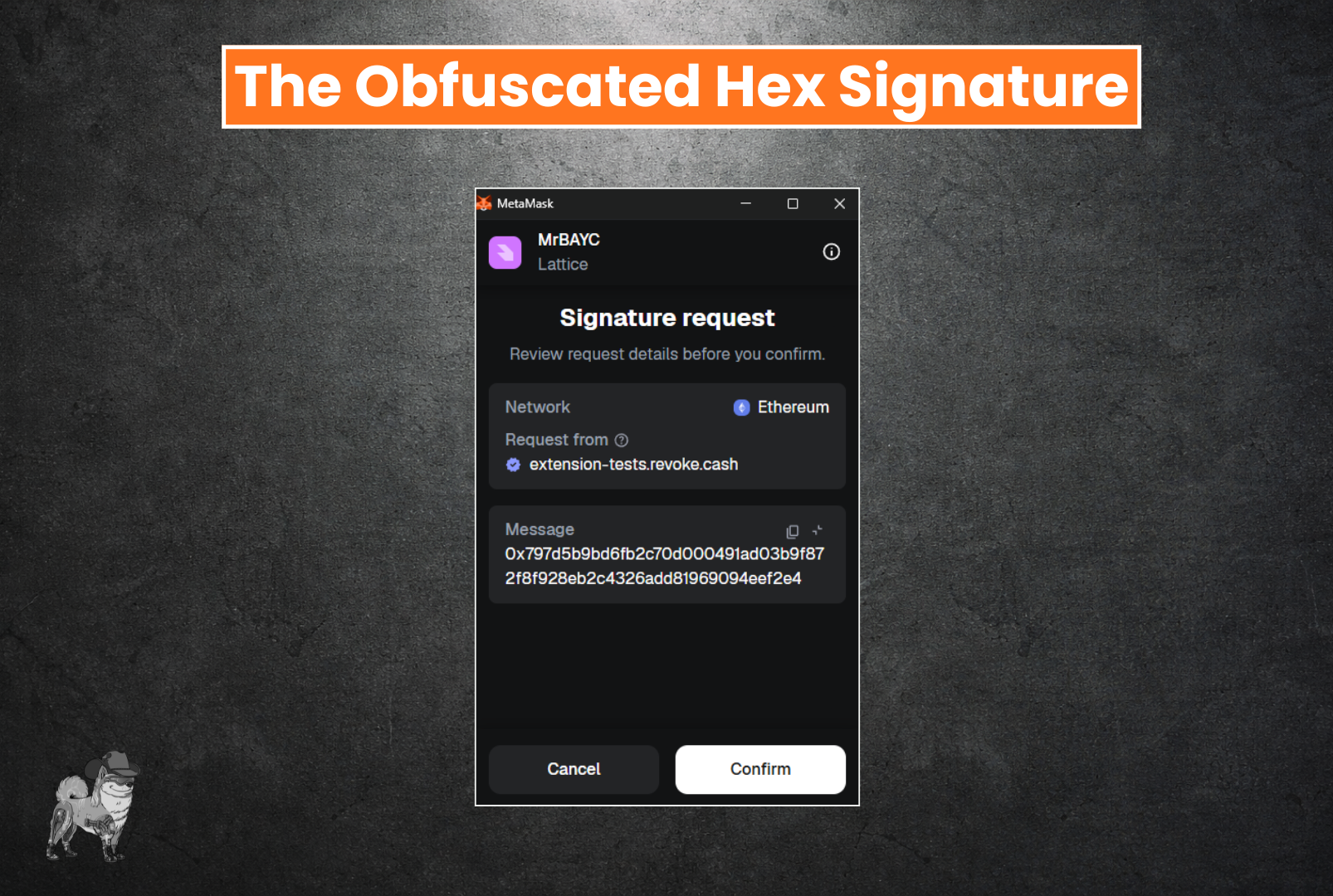
Type #3 - The Obfuscated Hex Signature (Use Extreme Caution!)
Now just because something doesn't have a beautifully typed signature in accordance with the EIP-712 standard above, doesn't mean its a scam. However, it does mean that you are trusting the counterparty with whatever message you may be signing, as you are essentially “Blind Signing” it. Although we are not seeing these leveraged on Opensea these days due to upgrades in the Seaport contract, other marketplaces and protocols still leverage them. I would be cautious, particularly if you are on a wallet address with open approvals. Not sure? Check out our article on revoking approvals and see what approvals you have open on that wallet address!
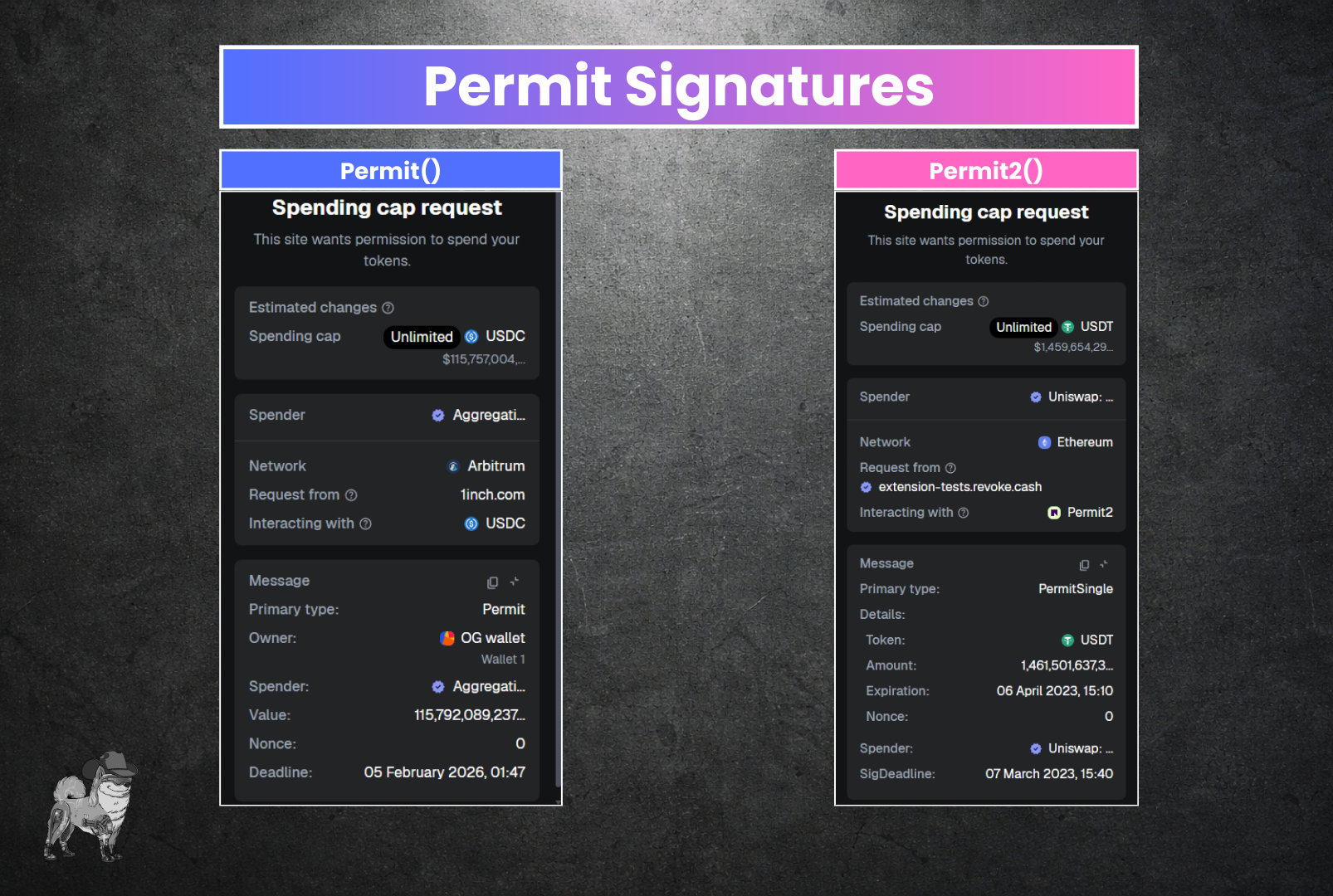
Type #4 - Permit Signatures
In our All About Approvals article, we go over a special signature type for some tokens that can grant permissions for certain ERC-20 tokens without first needing on-chain approval, called Permit (AKA EIP-2612). Some major tokens implement this feature, such as $USDC, $DAI, and other DeFi tokens across multiple EVM networks. This feature was later expanded by the UNILabs team to create a primitive that allows even tokens that don’t natively support Permit can be approved to this “Permit2” contract, and get all the functionality of Permit across the blockchain. Usage is slowly increasing over time, and soon, hopefully, the days of approving tokens to random dApps at all will be gone, as approvals are infinite and akin to leaving a backdoor open to your wallet in perpetuity, whereas Permit2 can have an expiry.
Type #5 - ETH_Sign - Deprecated (Dangerous!)
This is now a deprecated signature type, but it used to be pretty scary. For more information on this former signature type, take a look at this June 8, 2022.
Additional Resources
We understand that we are simplifying some of the technical terms here, so before you say, “You guys are using the wrong words for this!” just know that we are trying to simplify the framework to make this more understandable for all! Below are more resources and more technical explanations of signatures, signature types, and their implementations:
Some more helpful articles on Signatures:
- Intro to cryptography and Signatures in Ethereum - by Immunefi
- Signing Data | Metamask - by Metamask
- Permit2 by Uniswap Labs
Have any questions or want to learn more about web3 security and stay up to date on the most current security information, scams, and tactics? Join us in our discord at https://discord.gg/boringsecurity . ![]()

